Wallaroo DNS Configuration Guide
Table of Contents
DNS services integration is required for Wallaroo Enterprise to provide access to the various supporting services that are part of the Wallaroo instance. These include:
- Simplified user authentication and management.
- Centralized services for accessing the Wallaroo Dashboard, Wallaroo SDK and Authentication.
- Collaboration features allowing teams to work together.
- Managed security, auditing and traceability.
The following guide is for standard DNS services.
Once integrated, users can access the following services directly from a URL starting with the Wallaroo Domain - this is the domain name where other DNS entries are appended to. For example, if the Wallaroo Domain is wallaroo.example.com, then the other services would be referenced by https://wallaroo.sample.com/{service}.
Note that even when accessing specific Wallaroo services directly that the user must still be authenticated through Wallaroo.
| Service | Path | Description |
|---|---|---|
| Wallaroo Dashboard | wallaroo domain | Provides access to a user interface for updating workspaces, pipelines, and models. Also provides access to the integrated JupyterHub service. |
| API | v1/api | Provides access to the Wallaroo API. |
| Authentication | auth | Provides access to the Wallaroo Authentication Service. |
| Edge Observability | edge | Optional service for edge and multicloud deployments to report inference results back to the Wallaroo Ops instance. |
Connections to Wallaroo services are provided as https://{Wallaroo Domain}/service. For example, if the Wallaroo Domain is wallaroo.example.com then the URLs to access the various Wallaroo services would be:
- Base URL:
https://wallaroo.example.com - Wallaroo MLOps API:
https://wallaroo.example.com/v1/api - Authentication Service URL:
https://wallaroo.example.com/auth
Prerequisites
- Install Wallaroo Enterprise into a qualified environment. For more details, see the Wallaroo Install Guides and the Wallaroo Enterprise Install Guides.
- Determine whether your organization will use a prefix or not as detailed above.
- Generate the SSL Certificates. See How to update SSL Certificates for Wallaroo for instructions on generating SSL certificates and updating the Wallaroo instance with new certificates.
- Have access to internal corporate DNS configurations that can be updated. A subdomain for the Wallaroo instance will be created through this process.
- Install kubectl into the Kubernetes cluster administrative node.
Wallaroo IP Address Retrieval Methods
The first step is to retrieve the IP address connected to the Wallaroo load balancer for the cluster.
Retrieve LoadBalancer IP with kubectl
For most organizations that install Wallaroo into a cloud based Kubernetes cluster such as Microsoft Azure, AWS, etc the external IP address is tied to Wallaroo LoadBalancer service. This can be retrieved with the kubectl command as follows:
Retrieve the external IP address for your Wallaroo instance LoadBalancer. For example, this can be performed through the following
kubectlcommand:kubectl get svc api-lb-ext -n wallaroo -o jsonpath='{.status.loadBalancer.ingress[0].ip}'34.83.140.98An alternative to this command to show all services is the following:
kubectl get svc -AExample Result:
kubectl get svc -A NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE default kubernetes ClusterIP 10.25.64.1 <none> 443/TCP 50d gmp-system alertmanager ClusterIP None <none> 9093/TCP 50d gmp-system gmp-operator ClusterIP 10.25.70.18 <none> 8443/TCP,443/TCP 50d kube-system default-http-backend NodePort 10.25.67.38 <none> 80:31378/TCP 50d kube-system kube-dns ClusterIP 10.25.64.10 <none> 53/UDP,53/TCP 50d kube-system metrics-server ClusterIP 10.25.67.8 <none> 443/TCP 50d wallaroo alertconfig ClusterIP 10.25.67.141 <none> 9094/TCP 2m30s wallaroo alertmanager ClusterIP 10.25.77.167 <none> 9093/TCP 2m30s wallaroo api-lb ClusterIP 10.25.79.188 <none> 8080/TCP 2m31s wallaroo api-lb-admin ClusterIP 10.25.70.0 <none> 9901/TCP 2m31s wallaroo api-lb-ext LoadBalancer 10.25.69.9 34.83.140.98 80:30715/TCP,443:32664/TCP 2m31s wallaroo dashboard ClusterIP 10.25.72.14 <none> 4567/TCP 2m31s wallaroo wallsvc ClusterIP 10.25.75.74 <none> 3040/TCP 2m30sSome cloud providers may provide multiple external IP addresses for the
api-lbservice. For some services such as Oracle, this is typically a 10 net address, with the second IP address being the actual external address. Verify the IP address before changing DNS settings.
Other Methods
For organizations install Wallaroo other methods, such as Single Node Linux may find the kubectl get svc api-lb-ext command only returns the internal IP address.
Depending on the instance, there are different methods of acquiring that IP address. The links below reference difference sources.
- AWS: How do I get the ID and IP address of an Amazon EC2 instance for an AWS Batch job?
- GCP: Locating IP addresses for an instance
- Azure: IP addresses in Azure Functions
Refer to your Wallaroo support representative if further assistance is needed.
DNS Entries
Create DNS the following entries based on the list above for the Wallaroo instance’s IP address. Select the cloud environment used for DNS services.
Create DNS the following entries based on the list above for the Wallaroo instance’s IP address. Select the cloud environment used for DNS services.
- For AWS Clusters:
- Wallaroo domain: CN (CNAME) record referring to the AWS EKS cluster endpoint. For example:
wallaroo.example.com.
- Wallaroo domain: CN (CNAME) record referring to the AWS EKS cluster endpoint. For example:
- For all other cloud services:
- Wallaroo domain:
Arecord,NS(Name Server) record,SOA(Start Of Authority) record. For example:wallaroo.example.com
- Wallaroo domain:
- References:
Update DNS Services for Wallaroo
Select the method of updating DNS services based on the method of installing Wallaroo: kots or helm.
Update DNS Configuration for Wallaroo for Kots Installations
The following is for configuring DNS services in Wallaroo for a Kots based installation.
Access the Kots Administrative Dashboard in a browser. This can be done either after installation, or through the following command (assuming the Wallaroo instance was installed into the namespace
wallaroo). By default this provides the Kots Administrative Dashboard through the URLhttps://localhost:8800.kubectl kots admin-console --namespace wallarooFrom the Wallaroo Dashboard, select Config and set the following:
DNS Settings
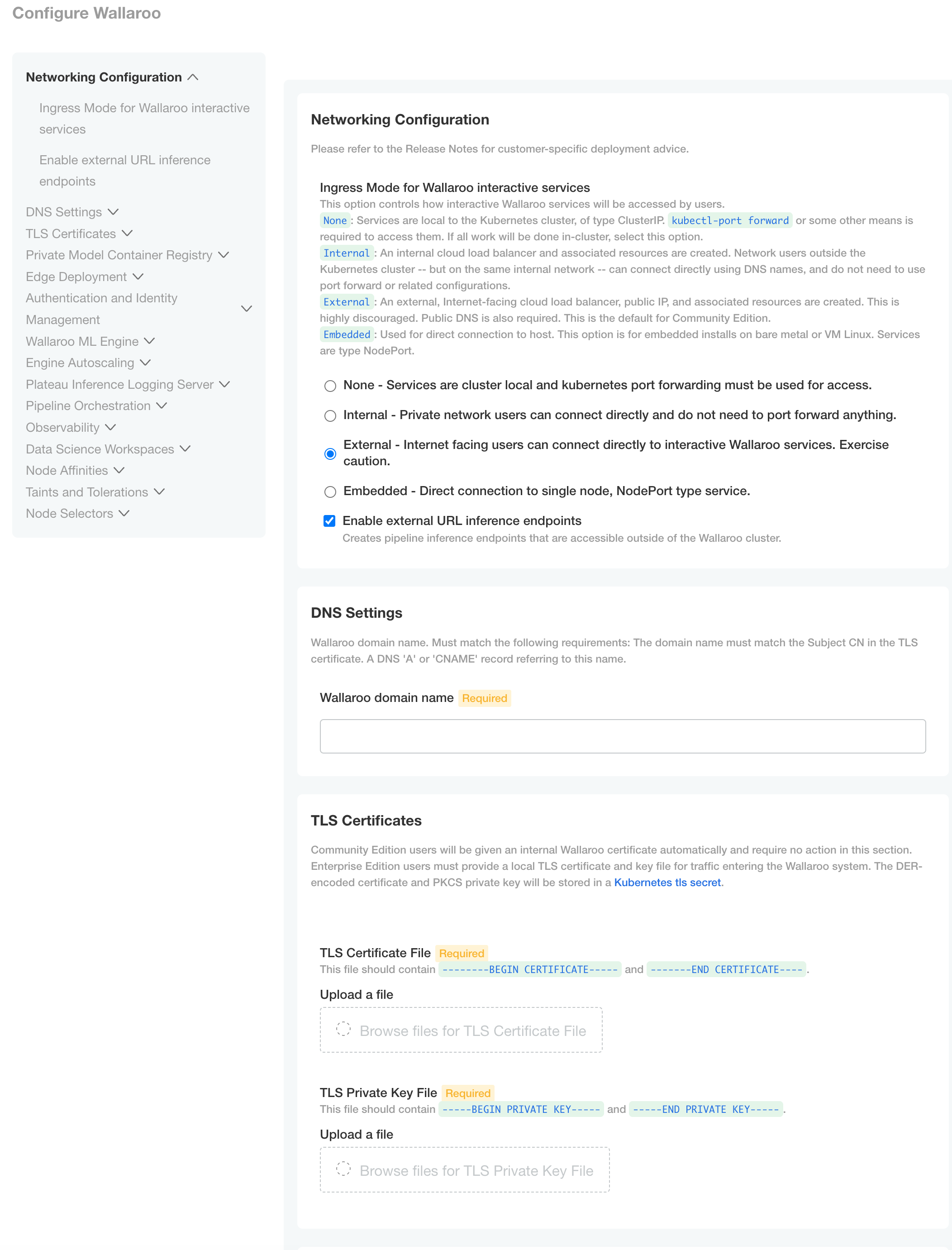
- Wallaroo domain name (Required): The domain for the Wallaroo instance.
Once complete, scroll to the bottom of the Config page and select Save config.
A pop-up window will display The config for Wallaroo Enterprise has been updated.. Select Go to updated version to continue.
From the Version History page, select Deploy. Once the new deployment is finished, you will be able to access Wallaroo services via their DNS addresses.
To verify the configuration is complete, access the Wallaroo Dashboard through the Wallaroo domain. For example if the Wallaroo domain is wallaroo.example.com then access https://wallaroo.example.com in a browser and verify the connection and certificates.
Update DNS Services for Helm Installations
The following instructions are for installations of Wallaroo in a Helm based installation. By default, the DNS settings for the Wallaroo instance are configured during the installation. For more information, see Helm Based Install Guides.
The following shows how to update the DNS and security certificates for existing Wallaroo installations.
Set the Wallaroo Domain Name for Helm
The Wallaroo domain name are set with the following Helm variables:
wallarooDomain: The DNS name for the Wallaroo instance.custTlsSecretName: The Kubernetes secret storing the certificate information.
The following is a minimum local-values.yaml file with the Wallaroo Domain set to wallaroo.example.com:
wallarooDomain: "wallaroo.example.com" # change to match the domain name
custTlsSecretName: cust-cert-secret
apilb:
serviceType: LoadBalancer
external_inference_endpoints_enabled: true
ingress_mode: internal # internal (Default), external,or none
dashboard:
clientName: "Wallaroo Helm Example" # Insert the name displayed in the Wallaroo Dashboard
kubernetes_distribution: "" # Required. One of: aks, eks, gke, oke, or kurl.
Update the
helmbased installation with thehelm upgradecommand in the following format:helm upgrade $RELEASE $REGISTRYURL --version $VERSION--values $LOCALVALUES.yaml --timeout 10mWhere:
$RELEASE: The name of the Helm release. By default,wallaroo.$REGISTRYURL: The URl for the Wallaroo container registry service.$VERSION: The version of Wallaroo to install. For this example,2024.2.1.$LOCALVALUES: The .yaml file containing the local values overrides. For this example,local-values.yaml.
For example, for the release
wallaroothe command would be:helm upgrade wallaroo oci://registry.replicated.com/wallaroo/2024-2/wallaroo --version 2024.2.1 --values local-values.yaml --timeout 10m
Edge Observability Enablement
For organizations that deploy Wallaroo pipelines on edge devices as Wallaroo Servers, see the DNS settings from the Edge Deployment Registry Guide.